Since the onset of remote work, major ransomware attacks are now constantly filling up our news feeds. A new ransom record is broken every other day and the attacks are becoming increasingly sophisticated and severe for businesses. It’s become such an issue that politicians and governments around the world are beginning to feel the pressure to take action.
But don’t wait on them to do something.
Here are 5 steps you can take now to prevent your company from becoming the next headline.
What is Ransomware?
Ransomware is malicious software used for the purpose of accessing and encrypting computers and their associated networks. If you were to unknowingly download ransomware, say through mistaking a phishing email as genuine, this would compromise your personal system and likely encrypt your data until you have paid the demanded ransom. Failure to do so may result in the ransom price doubling or the leaking of private company data.
Below is an example image of what your computer may show in the event of a successful REvil attack. Learn how to protect your business so that you will greatly reduce the probability of experiencing something similar.
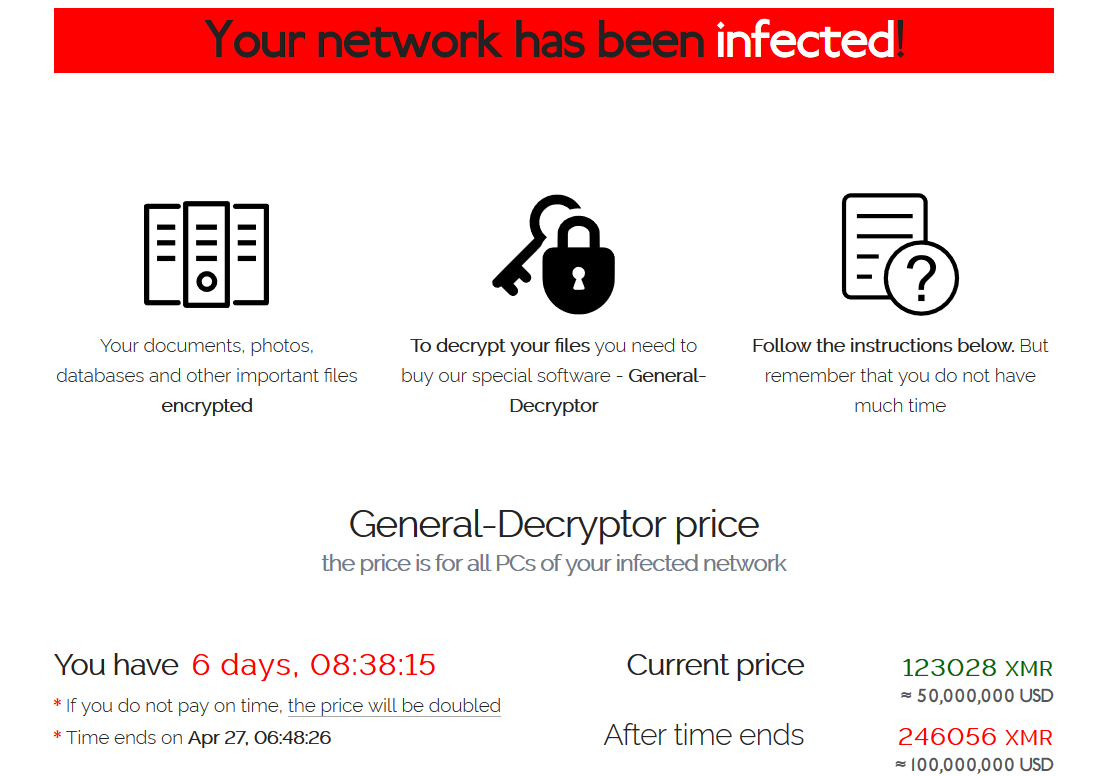
-
Regularly backup your data
Long considered the greatest method of ransomware recovery, systems backups aren’t as foolproof as they once were. Attackers may now encrypt your data twice, steal intellectual property, employee data, proprietary information, or customer information.
Next-gen ransomware may also have the capability of seeking out backup locations and destroying them. However, this doesn’t mean they aren’t effective. Having a secure backup in a separate location and/or in the cloud is vital to ensuring you can continue to operate in the event of an attack and afford to not pay a ransom.
-
Invest in employee security training
A large proportion of cyber incidents are caused by negligent employees. Whether they click on a phishing link or input their work email and password into a fake website, the result is the same – a compromised network and massive incurred costs.
Employees must be taught how to operate computers safely as they’re much bigger danger than meets the eye. The cyber threat environment is always changing as threat actors explore the next innovative method to secure their payday, therefore training must be kept updated and consistent.
For example, a sporadic simulated phishing campaign can gauge how vigilant your employees are to breaching attempts post-training.
-
Segment your network
Network segmentation involves the creation of smaller network partitions via the use of firewalls or virtual LANs, among other techniques. This serves as an extra few layers of protection against attackers. For instance, if one area of a network is breached then the malware or threat actor cannot freely infiltrate and modify the entire network.
Typically, large enterprises employ these techniques for customer-facing services, or by data type. If you would like more information on network segmentation and how it may benefit your businesses security, please don’t hesitant to get in touch.
-
Conduct regular network security assessments
Organisations are held to certain compliance standards when it comes to cybersecurity (e.g., NIST or HIPAA). Generally, they require quarterly vulnerability scans and annual penetration testing. However, we recommend these procedures be carried out much more frequently and become a habitual part of your operations.
For example, Evisent utilises automated reporting accessible through Microsoft Teams that provides real time information on your security posture and adherence to modern compliance standards.
This means you can check your areas of vulnerability at any time without having to rely on an end of month security report from your MSP. This level of transparency allows you to have confidence in the recommendations we provide to improve your security as everything is backed by clear data.
-
Use a password manager
Compromised passwords are the leading cause of successful breaches. The transition towards remote work has only increased the popularity of brute-force attacks targeting remote desktop credentials and employees through phishing.
To mitigate these concerns, organisations must use robust password security protocols. Beginning with a password manager is a good start (e.g., LastPass, Dashlane, or Keeper). These allow for unique and complex passwords for every individual account. We also suggest mandating the use of multi-factor authentication (2FA) wherever you can.
Ransomware attacks can be extremely costly, not only financially but keeping in mind potential damage to company reputation and customer loyalty. It’s important that you take these initial steps to remain proactive in the face of the inevitable. If you’ve already done this and would like to learn more about what you can do to secure your business, contact Evisent today for a free security consultation.